It is 7:55 am and your employee is rushing to her desk to start her computer and join an important morning web conference. She breathes a sigh of relief, realizing she’ll be able to connect on time.
But then disaster strikes...
Your IT department's policy requires a new password every 30 days and today is the day. She must come up with a new password (using mixed case letters, numbers, and special characters). She decides to reuse an old password, but adds the number 2 to the end. Oops, that doesn’t work… she did that the last time. She keeps trying and finally gets lucky with the number 5. She must now log out and log back in so that the new password is propagated across other services.
Now she’s late for the call, but at least her computer is more secure now.
Or is it?
Research has shown that requiring frequent password changes actually decreases computer security. According to a report by the UK government’s National Cyber Security Centre (NCSC), “Regular password changing harms rather than improves security, so avoid placing this burden on users.”
It’s no secret that humans are poor at remembering random sequences of characters. We may be able to remember a few important sequences (such as phone numbers) but as soon as we need to remember more than a handful of passwords, we often resort to “tricks” to help with memorization.
Writing passwords on Post-it notes is one such trick. Adding a number or a special character to a simple word or an existing password is another. So when companies require employees to invent new passwords to log into their computers every few months, employees predictably resort to using passwords like “Password!” that are easy to remember but extremely insecure.

designer491/iStock/Getty Images Plus
Malicious actors understand human nature and start with obvious passwords like “Password!” when they are infiltrating a system. And for complex mathematical reasons, passwords that are almost identical are far easier to crack than a password that never changes.
To make matters worse, if a password has been discovered, changing the password in 30 days is unlikely to help. When attackers gain access to a system, they exploit it immediately rather than waiting 30 days. They also install tools, such as password loggers, just in case the password is changed, so they’ll get the new password as well.
Where did the idea of requiring regular passwords changes come from? In 2003, the National Institute of Standards and Testing (NIST) released a report that recommended regular password changes within organizations, in order to increase cyber security1. Many IT departments adopted this recommendation, because it was an easy rule to enforce and it showed management they were looking after security.
Today however, NIST explicitly requires that organizations (especially US government ones) NOT force users to change their passwords on a regular basis2. And in May 2019, Microsoft published security guidelines that recommend companies not require user password changes on a fixed schedule.
Both NIST and the UK government also recommend that users NOT be required to use the complex mix of numbers, letters, and punctuation known in the security world as composition rules. According to NIST, “Composition rules also inadvertently encourage people to use the same password across multiple systems since they often result in passwords that are difficult for people to memorize.” A number of cyber security authorities around the world now discourage enforced policies on password complexity and expiry. Unfortunately, these policies still prevail throughout many organizations.
Related articles
- BC AWARE discusses cybersecurity for the decade ahead
- Cloudy with a chance of a data leaks: What business professionals need to know before using the cloud
How to enforce strong passwords
What should companies be asking their employees to do instead? First of all, never reuse passwords, especially across systems. Each password should be completely different from any previous password you have used.
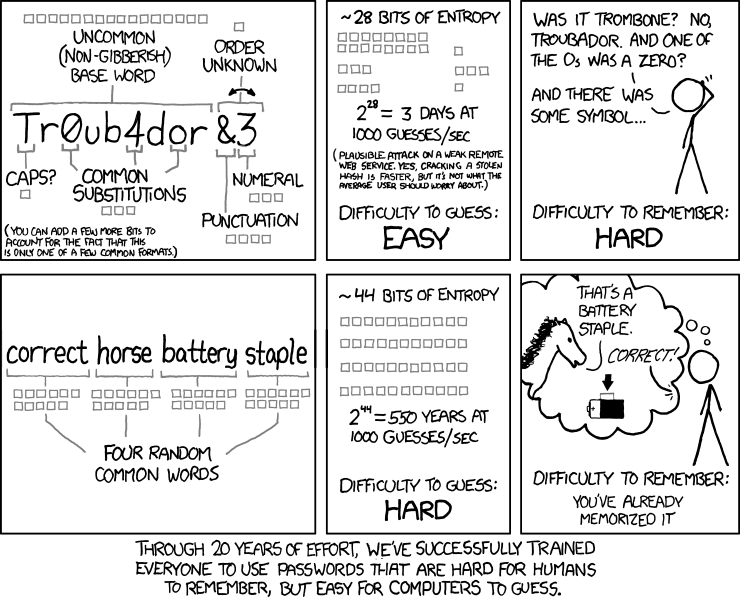
Secondly, create passwords that will never be found in a dictionary. The NCSC recommends creating passwords using three random words, such as 'coffeetrainfish' or ‘walltinshirt’. This is a good strategy and the famous techie cartoon xkcd shows why this works:
Don’t try to get cute and substitute numbers for letters (such as “5” for “s”) as cyber criminals are already onto this and regularly try passwords like “Pa55w0rd.”
How to manage your passwords
Now, if you are like me, you may have hundreds of personal and business accounts that require passwords, so memorizing them all is impossible. Instead of writing them down, companies should require that employees use a password management app. Most of these apps will synchronize passwords across different devices, making it easier to log on from any location. Some good examples of password management apps include LastPass, 1Password, and BitWarden (which is free).
Ultimately, most security professionals hope passwords will die out soon, to be replaced with far better technologies like multifactor authentication (MFA). In the meantime, if employees make every password different, ideally from a string of three or four random words, and store them in a good password management app, and IT departments eliminate password expiration, an organization can increase its online security while also making everyone’s login experiences a lot easier.
Eric Byres, P.Eng, ISA Fellow, is an expert in ICS and IIoT security. Experienced in controls engineering, security research and corporate management, he blends deep technical knowledge with practical business experience. He has led international standards development, and created the Tofino Firewall, the world’s most widely deployed ICS security appliance.
1 National Institute of Standards and Testing, Special Publication 800-63 – Appendix A, 2003
2 National Institute of Standards and Testing, Special Publication 800-63B - Digital Identity Guidelines, Section 5.1.1.2, June 2019.